At the end of July 2025 — so almost 6 months ago — we launched the second RP2350 Hacking Challenge, searching for practical side-channel attacks on the power-hardened AES implementation underpinning RP2350‘s secure boot. So far, we don’t have a winner, so we decided to evolve the challenge by removing one of the core defense-in-depth features: the randomisation of memory accesses.

Our AES implementation was designed to withstand side-channel attacks by using multi-way secret sharing (where sensitive values are split into random components that must be XORed together) and by randomly permuting the order of operations and data. We hope that even just the multi-way shares are enough to protect us against side-channel attacks; hence, we have decided to update our challenge:
If you manage to demonstrate a successful attack on our AES implementation without the randomisation, you win!
What’s changed?
We’ve disabled the different randomisation features, such as VPERM and BPERM, and removed the jitter to make collecting good measurements easier — your traces should align much more nicely now! We’ve also added a Unicorn-based emulation example, in the hope that people without fancy hardware setups can build virtual power-analysis attacks.
You can see these changes reflected in the Hacking Challenge 2 GitHub repository.
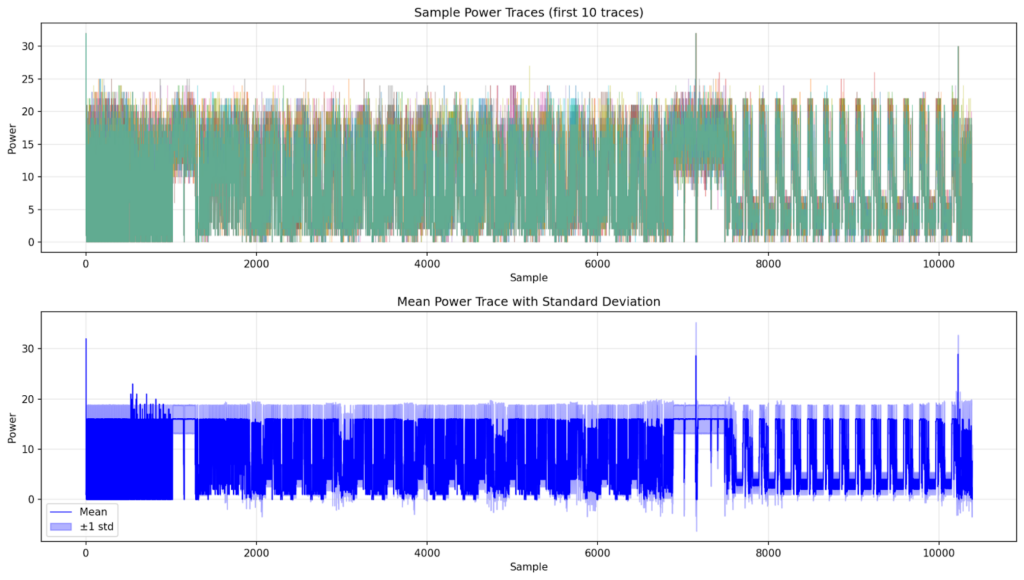
Example (cleaned-up) power traces collected from the target — the rounds are clearly visible
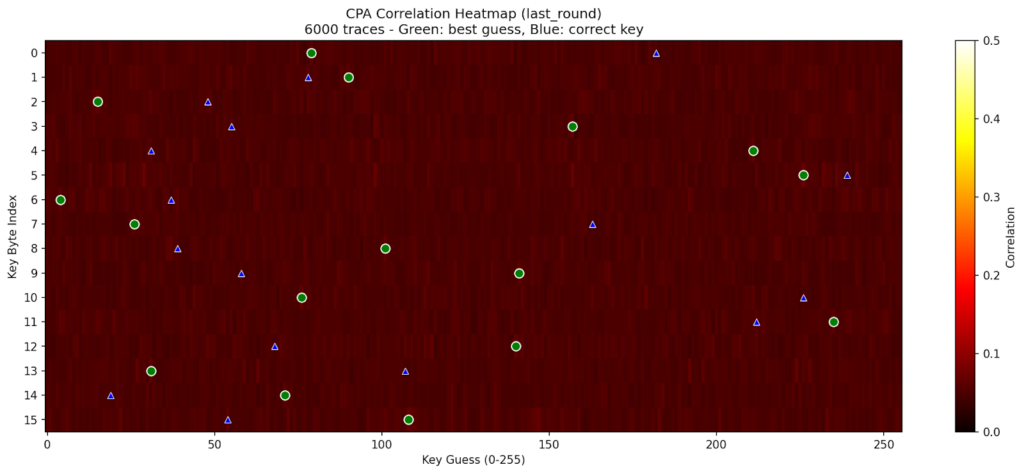
An example of our analysis on the last round; we could not identify a strong correlation between our power analysis and the correct key I didn’t understand any of this?!
The secure boot protection of firmware on RP2350 relies on AES — the Advanced Encryption Standard — to decrypt the firmware from external flash into the on-chip SRAM. AES in itself is considered very secure; however, a lot of software and hardware implementations are susceptible to so-called side-channel attacks. By recording and analysing hundreds of thousands (or even millions) of power traces on the chip, attackers might be able to recover the encryption key.
To protect against this, we worked with some very smart folks to build an AES implementation that is hardened against these kinds of attacks. Now we are putting it to the test by offering a bounty to the first person who successfully manages to attack our AES via side channels!
I’m almost there…
Getting close but don’t have a successful attack yet? Write to us! We care more about protecting our implementation than about having a full end-to-end attack. If you’ve identified a leak, we want to talk to you!

What we know so far
During our initial work on the AES implementation, we found some abstract correlation that lets us differentiate between an all-zeros key and an all-ones key. However, we were unable to build a model that significantly impacts the key space.
A bit more time on the clock
To give you a little more time to keep hacking, we’re extending the deadline to 30 April 2026. The prize remains unchanged at $20,000.
Head to the Hacking Challenge 2 repo to view the updated challenge software.
The post RP2350 Hacking Challenge 2: Less randomisation, more correlation appeared first on Raspberry Pi.
Source: https://www.raspberrypi.com/news/rp2350 ... rrelation/
